What is Phishing?
Phishing is when cybercriminals try to steal personal information such as passwords, credit cards, and social security numbers through email and websites. Over 90% of cyberattacks against organizations are through phishing emails.
If I receive a suspicious email, what should I do?
- If you are unsure of the email, do not click any links, respond to the sender, or download any attachments.
- Try calling the sender and speak with them directly to confirm whether or not the email is legitimate. If you respond via email, the cybercriminal will continue to pretend to be the sender and encourage you to follow through with the original request.
- Report this immediately by forwarding the email to sos@npsgglobal.com. The IT department will review the email to determine whether or not it is a legitimate email.
What should I do if I think my account has been compromised by disclosing personal information through a phishing email, or if I downloaded an attachment that might have had malware on it?
- Change your password immediately. You can hold down the CTRL-ALT-DEL keys and choose “Change a password” to start this process on a Windows computer owned by NPSG.
- Turn off your computer and alert IT by sending an email to sos@npsgglobal.com
- If you use your password on other sites such as your banking account, you should immediately change your password there as well.
How Can I Detect Phishing e-mails?
You should check several different components of an email including the sender, who the message is sent to, the subject line, attached links, message body, and signature line. If you detect a few of these warning signs, you should be suspect of the email as a potential phishing email. Here are a few recent examples and warning signs. If you receive an email that has several warning signs, you should be suspicious of the email as a potential phishing attempt.
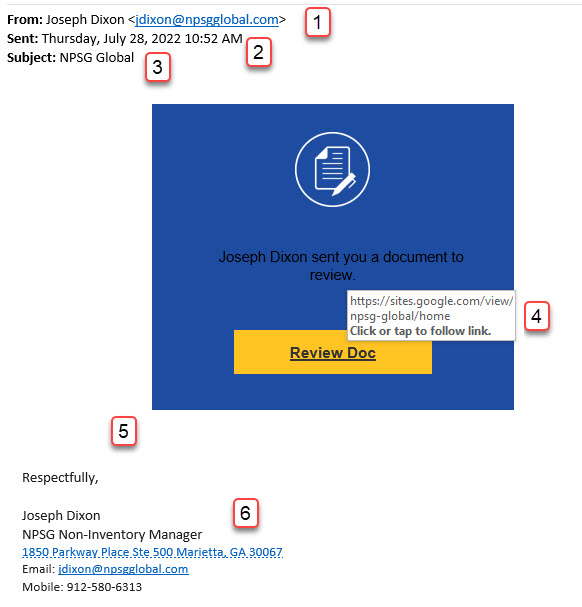
E-mail Example 1:
- Sender – Is the sender someone you know and who you routinely communicate with or is this the first time you have ever received a communication from them? If it is someone you have not communicated with before, that doesn’t mean it is a phishing attempt, but if they are asking you to click a link or download a file, you should be suspicious. This is a warning sign.
- To – Always check to see who is the email sent to. In this case, there is no one in the TO field. Phishing attacks are sometimes sent as mass emails to numerous recipients using the BCC field. That was the case for this email. This should be a warning sign.
- Subject – Is the email subject specific or vague? In this case, “NPSG Global” is a very generic subject line. This should be a warning sign.
- Links – If there are links in the email, be suspicious if it is to a site you do not recognize or one that is not routinely used by our organization. You can hover your mouse over a link, without actually clicking the link, to view the actual link sent in the email. We routinely use Teams and SharePoint. In this case, the link was to Google which is not a site our organization normally uses to send or share documents. In addition, the image used in the emails is an image normally used for a DocuSign request, which also does not match the Google link. These are both warning signs.
- Message – What is the message in the email? In this case, there is no message at all. This should be a warning sign.
- e-mail Signature – Just because everything is correct in the email signature, that doesn’t mean that the email is legitimate. It is easy to use someone’s existing signature, or copy the signature from an old email, to help make it appear that the email is real.
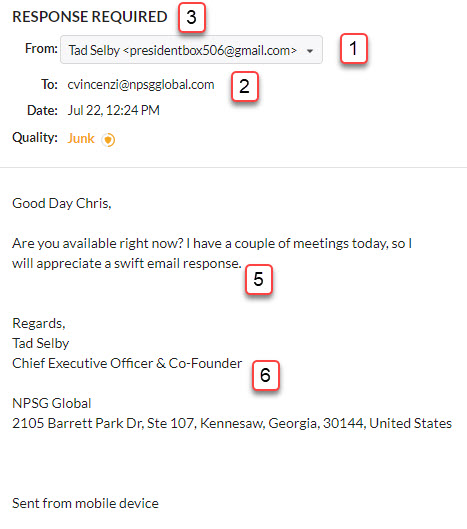
E-mail Example 2:
- Sender – Check the sender to see if the email address machines the person sending the email. In this case, although the email says it is from Tad Selby, the actual email address is from “presidentbox506″ and it is a G-mail address. Both of these are warning signs and you should be very suspicious of emails coming from an outside email addresses where the name is that of an NPSG employee.
- To – In this case, the email was sent directly to the recipient. There is no warning sign here.
- Subject – The subject line is in all caps “RESPONSE REQUIRED”. Many times, phishing emails are sent as urgent requests, or in a threatening tone, that must be replied to immediately. This is because the cybercriminals know that they only have a short window of time before they are caught and are looking to get people to respond back quickly with personal information. In addition, this is another generic subject line. These are warning signs.
- Links – There are no links in the original email. In this type of attack, had I responded, the cybercriminal would have likely requested me to purchase gift cards and send the information to them while pretending to be Tad. This is another common scheme for cybercriminals.
- Message – Once again, the cybercriminal is trying to get a quick reply back in asking for a “swift response” and is trying to avoid any phone calls or other direct communication with Tad by claiming to be in meetings and needing an email response.
- e-mail Signature – In this case, the email is signed with our old mailing address. Definitely a warning sign.